350-701 Dumps Updated | 350-701 (SCOR) Quick Preparation Materials
If you’re busy and want to prepare for the Cisco 350-701 (SCOR) exam quickly, we’ve prepared the latest 350-701 dumps as 350-701 (SCOR) quick preparation material for your exam to help you pass the exam.
We have updated the 350-701 dumps webpage https://www.pass4itsure.com/350-701.html with new 542 answers questions for an exam that will be a powerful preparation material for you.

Will you introduce the latest Cisco 350-701 exam?
The Cisco 350-701 exam is full name Implementing and Operating Cisco Security Core Technologies, and you can also call it the 350-701 SCOR exam.
In a real exam, you need to answer 90-110 questions in 120 minutes and score 750-850 to pass. It costs $400 to take the exam.
Certifications related to the 350-701 exam are:
CCNP Security Certification – CCNP Security Core Exam (350-701)
CCIE Security Certification – CCIE Security Qualifying Exam (350-701)
Cisco Certified Specialist Certification – Security Core (350-701)
Since the 350-701 SCOR exam is not easy, how do I prepare for it quickly?
As we all know, the 350-701 exam is not a simple level of exam, you need to spend energy preparing carefully to pass.
You should prepare for the 350-701 SCOR exam quickly like this:
The first thing you need to do is choose a Pass4itSure 350-701 dumps as your quick preparation material.
Then go for regular practice of exam questions to achieve proficiency.
Finally, take the exam with confidence in victory.
Are the Pass4itSure 350-701 dumps always valid?
Pass4itSure always follows this real exam and prepares the material, so Pass4itSure 350-701 dumps are always updated and always valid.
Where can I download valid 350-701 dumps?
We share with you the latest 350-701 exam dumps PDF free download: https://drive.google.com/file/d/1yART2yVVxbMXjGG0WHPiiHxYMv3v6Fs3/view?usp=sharing [google drive]
350-701 Free Dumps Practice Exam Questions and Answers
NEW QUESTION 1
How is DNS tunneling used to exfiltrate data out of a corporate network?
A. It corrupts DNS servers by replacing the actual IP address with a rogue address to collect information or start other attacks.
B. It encodes the payload with random characters that are broken into short strings and the DNS server rebuilds the exfiltrated data.
C. It redirects DNS requests to a malicious server used to steal user credentials, which allows further damage and theft on the network.
D. It leverages the DNS server by permitting recursive lookups to spread the attack to other DNS servers.
Correct Answer: B
Domain name system (DNS) is the protocol that translates human-friendly URLs, such as securitytut.com, into IP addresses, such as 183.33.24.13. Because DNS messages are only used at the beginning of each communication and they are not intended for data transfer, many organizations do not monitor their DNS traffic for malicious activity. As a result, DNS-based attacks can be effective if launched against their networks. DNS tunneling is one such attack.An example of DNS Tunneling is shown below:
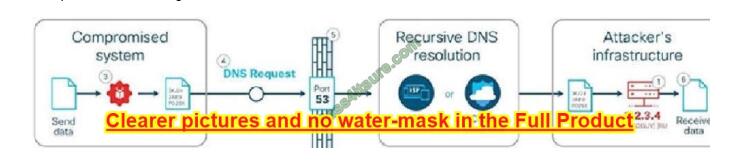
The attacker incorporates one of many open-source DNS tunneling kits into an authoritative DNS nameserver (NS) and malicious payload.2. An IP address (e.g. 1.2.3.4) is allocated from the attacker\\’s infrastructure and a domain name (e.g. attackerdomain.com) is registered or reused. The registrar informs the top-level domain (.com) nameservers to refer requests for attackerdomain.com to ns.attackerdomain.com, which has a DNS record mapped to 1.2.3.43. The attacker compromises a system with a malicious payload.
Once the desired data is obtained, the payload encodes the data as a series of 32 characters (0-9, A-Z) broken into short strings (3KJ242AIE9, P028X977W,…).4. The payload initiates thousands of unique DNS record requests to the attacker\\’s domain with each string as
Reference: https://learnumbrella.cisco.com/i/775902-dns-tunneling/0
NEW QUESTION 2
What is a language format designed to exchange threat intelligence that can be transported over the TAXII protocol?
A. STIX
B. XMPP
C. pxGrid
D. SMTP
Correct Answer: A
TAXII (Trusted Automated Exchange of Indicator Information) is a standard that provides a transport
NEW QUESTION 3
Which product allows Cisco FMC to push security intelligence observable to its sensors from other products?
A. Encrypted Traffic Analytics
B. Threat Intelligence Director
C. Cognitive Threat Analytics
D. Cisco Talos Intelligence
Correct Answer: B
NEW QUESTION 4
What is the benefit of using Cisco Umbrella?
A. DNS queries are resolved faster.
B. Attacks can be mitigated before the application connection occurs.
C. Files are scanned for viruses before they are allowed to run.
D. It prevents malicious inbound traffic.
Correct Answer: B
NEW QUESTION 5
A network engineer must monitor user and device behavior within the on-premises network. This data must be sent to the Cisco Stealthwatch Cloud analytics platform for analysis. What must be done to meet this requirement using the Ubuntu-based VM appliance deployed in a VMware-based hypervisor?
A. Configure a Cisco FMC to send syslogs to Cisco Stealthwatch Cloud
B. Deploy the Cisco Stealthwatch Cloud PNM sensor that sends data to Cisco Stealthwatch Cloud
C. Deploy a Cisco FTD sensor to send network events to Cisco Stealthwatch Cloud
D. Configure a Cisco FMC to send NetFlow to Cisco Stealthwatch Cloud
Correct Answer: B
Reference: https://www.ciscolive.com/c/dam/r/ciscolive/us/docs/2019/pdf/5eU6DfQV/LTRSEC-2240-LG2.pdf
NEW QUESTION 6
Which solution stops unauthorized access to the system if a user\’s password is compromised?
A. VPN
B. MFA
C. AMP
D. SSL
Correct Answer: B
NEW QUESTION 7
An engineer enabled SSL decryption for Cisco Umbrella intelligent proxy and needs to ensure that traffic is inspected without alerting end-users. Which action accomplishes this goal?
A. Restrict access to only websites with trusted third-party signed certificates.
B. Modify the user\’s browser settings to suppress errors from Cisco Umbrella.
C. Upload the organization root CA to Cisco Umbrella.
D. Install the Cisco Umbrella root CA onto the user\’s device.
Correct Answer: D
NEW QUESTION 8
Which term describes when the Cisco Firepower downloads threat intelligence updates from Cisco Talos?
A. consumption
B. sharing
C. analysis
D. authoring
Correct Answer: A
… we will showcase Cisco Threat Intelligence Director (CTID) an exciting feature on Cisco\’s FirepowerManagement Center (FMC) product offering that automates the operationalization of threat intelligence. TID has the ability to consume threat intelligence via STIX over TAXII and allows uploads/downloads of STIX and simple blacklists.
NEW QUESTION 9
A Cisco FTD engineer is creating a new IKEv2 policy called s2s00123456789 for their organization to allow for additional protocols to terminate network devices. They currently only have one policy established and need the new policy to be a backup in case some devices cannot support the stronger algorithms listed in the primary policy.
What should be done in order to support this?
A. Change the integrity algorithms to SHA* to support all SHA algorithms in the primary policy
B. Make the priority for the new policy 5 and the primary policy 1
C. Change the encryption to AES* to support all AES algorithms in the primary policy
D. Make the priority for the primary policy 10 and the new policy 1
Correct Answer: B
NEW QUESTION 10
What are the two benefits of using Cisco Duo as an MFA solution? (Choose two.)
A. grants administrators a way to remotely wipe a lost or stolen device
B. provides a simple and streamlined login experience for multiple applications and users
C. native integration that helps secure applications across multiple cloud platforms or on-premises environments
D. encrypts data that is stored on endpoints
E. allows for centralized management of endpoint device applications and configurations
Correct Answer: BC
NEW QUESTION 11
Which technology limits communication between nodes on the same network segment to individual applications?
A. serverless infrastructure
B. micro-segmentation
C. SaaS deployment
D. machine-to-machine firewalling
Correct Answer: B
NEW QUESTION 12
In which two ways does a system administrator send web traffic transparently to the Web Security Appliance? (Choose two)
A. configure Active Directory Group Policies to push proxy settings
B. configure policy-based routing on the network infrastructure
C. reference a Proxy Auto-Config file
D. configure the proxy IP address in the web browser settings
E. use Web Cache Communication Protocol
Correct Answer: CE
NEW QUESTION 13
What is a characteristic of Firepower NGIPS inline deployment mode?
A. ASA with Firepower module cannot be deployed.
B. It cannot take actions such as blocking traffic.
C. It is out-of-band from traffic.
D. It must have inline interface pairs configured.
Correct Answer: D
Keep in mind that the 350-701 (SCOR) quick preparation material is a Pass4itSure 350-701 dumps (updated), get it here.