New 300-410 dumps (Including 2023 Newest Simulation Labs) for CCNP Enterprise ENARSI certification exam preparation
New 300-410 dumps containing 807 latest exam questions and answers are the best materials for preparing for the CCNP Enterprise ENARSI certification exam!
New 300-410 dumps are edited and corrected by the Cisco expert team. Participate in real scenarios to verify that it is true and effective, which can ensure 100% success in passing the CCNP Enterprise ENARSI certification exam.
Download New 300-410 dumps: https://www.pass4itsure.com/300-410.html, use PDF or VCE tools to help you learn easily, for CCNP Enterprise ENARSI certification exam preparation.
Share some of the New 300-410 dumps exam questions online practice(Include 2023 Newest Simulation Labs):
| From | Number of exam questions | Associated certifications | Exam prep |
| Pass4itsure | 15 | CCNP Enterprise | 300-410 |
Question 1:
Refer to the exhibit.
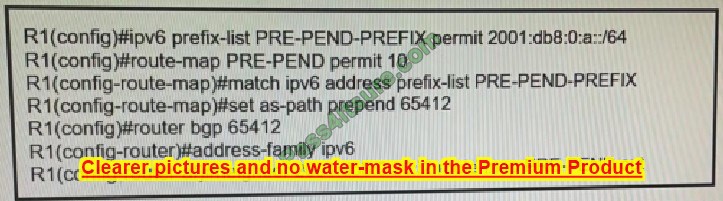
R1 has a route map configured, which results in a loss of partial IPv6 prefixes for the BGP neighbor, resulting in service degradation. How can the full service be restored?
A. The neighbor requires a soft reconfiguration, and this will clear the policy without resetting the BGP TCP connection.
B. The prefix lit requires all prefixes that R1 is advertising to be added to it, and this will allow additional prefixes to be advertised.
C. The route map requires a deny 20 statement without set conditions, and this will allow additional prefixes to be advertised.
D. The route map requires a permit 20 statement without set conditions, and this will allow additional prefixes to be advertised.
Correct Answer: D
Question 2:
What are the two functions of IPv6 Source Guard? (Choose two.)
A. It works independently from IPv6 neighbor discovery.
B. It denies traffic from unknown sources or unallocated addresses.
C. It uses the populated binding table for allowing legitimate traffic.
D. It denies traffic by inspecting neighbor discovery packets for specific patterns.
E. It blocks certain traffic by inspecting DHCP packets for specific sources.
Correct Answer: BC
IPv6 source guard is an interface feature between the populated binding table and data traffic filtering. IPv6 source guard can deny traffic from unknown sources or unallocated addresses.
Question 3:
Which parameter does EIGRP use to compute the bandwidth part of the metric?
A. The maximum bandwidth link in the path, in kilobits per second
B. The minimum bandwidth link in the path, in kilobits per second
C. The average bandwidth of all the links in the path, in kilobits per second
D. The average bandwidth of all the links in the path, in kilobytes per second
Correct Answer: B
The minimum bandwidth link, in kilobits per second, is used in the EIGRP metric calculation because this is the limiting factor in the overall speed of delivery over the path.
BW = (10,000,000 / bandwidth in Kbps) x 256
Delay = (delay in microseconds / 10) x 256
The formula for calculating the EIGRP metric is shown below:
[K1 x BW + (K2 X BW) / (256 – load) + K3 x delay] X [K5 / (reliability + K4)]
You should note, however, that when K5 = 0 (as it is by default), a slightly different formula applies.
When K5 = 0, the EIGRP metric is [K1 X BW + (K2 X BW) / (256 – load) + K3 x delay]
By default, K1 = 1, K3 = 1, and K2, K4, and K5 = 0.
Therefore, the default EIGRP metric is BW + Delay, where “BW” and “Delay” are determined according to the formula above.
The final formula is shown below:
[10,000,000 / (bandwidth in Kbps) + (delay in microseconds) / 10] * 256
These usually are derived from the values listed in the show interfaces command.
Objective:
Layer 3 Technologies
Sub-Objective:
Describe and optimize EIGRP metrics
References:
Cisco > Home > Support > Technology Support > IP Routing > Technology Information > Technology White Paper > Enhanced Interior Gateway Routing Protocol > Using The Metrics
Question 4:
Refer to the following output:
Router#show ip nhrp detail
1.1.2/8 via 10.2.1.2, Tunnel1 created 00:00:12, expire 01:59:47 TypE. dynamic, Flags: authoritative unique nat registered used NBMA address:
10.12.1.2
What does the authoritative flag mean in regard to the NHRP information?
A. It was obtained directly from the next-hop server.
B. Data packets are process switches for this mapping entry.
C. NHRP mapping is for networks that are local to this router.
D. The mapping entry was created in response to an NHRP registration request.
E. The NHRP mapping entry cannot be overwritten
Correct Answer: A
Question 5:
Which two solutions are used to overcome a flapping link that causes a frequent label-binding exchange between MPLS routers? (Choose two)
A. Create link dampening on links to protect the session.
B. Increase input queue on links to protect the session.
C. Create targeted hellos to protect the session.
D. Increase a hold-timer to protect the session.
E. Increase a session delay to protect the session.
Correct Answer: AC
To avoid having to rebuild the LDP session altogether, you can protect it. When the LDP session between two directly connected LSRs is protected, a targeted LDP session is built between the two LSRs.
When the directly connected link does go down between the two LSRs, the targeted LDP session is kept up as long as an alternative path exists between the two LSRs.
For the protection to work, you need to enable it on both LSRs. If this is not possible, you can enable it on one LSR, and the other LSR can accept the targeted LDP Hellos by configuring the command mpls ldp discovery targeted-hello accept
Reference:https://www.ccexpert.us/mpls-network/mpls-ldp-session-protection.html Or from the reference at https://www.ciscolive.com/c/dam/r/ciscolive/us/docs/2019/pdf/5eU6DfQV/TECMPL-3201.pdf Troubleshooting LDP Issues Problem:
I. When a link flaps (for a short time), the Solution:
+ When the LDP session supported by link hello is set up, create a targeted hello to protect the session.
Question 6 (2023 Labs):
Company A recently acquired Company B and the network infrastructures are being merged. Both organizations used non-overlapping globally unique network addressing but different Interior Gateway Protocols (IGPs).
Initially, multiple WAN links will connect the two organizations. Company A will maintain its core routing protocol, and Company B\’s routing protocol will be the edge routing protocol. Two-way redistribution will be used to ensure full network routing capability.
What additional routing configuration should be performed to prevent routing loops and suboptimal routing?
A. Manually configure static routes.
B. Manually configure default routes.
C. Manually adjust the administrative distances.
D. Manually adjust the local preference attribute.
Correct Answer: C
When routes are being redistributed from the core into the edge and from the edge into the core, the administrative distance (AD) associated with external routes should be modified.
This lessens the possibility of sub-optimal routing when multiple routing protocols advertise different paths to the same network.
The AD associated with the externally advertised routes should be higher than the internal IGP\’s AD. To change the AD for an entire routing protocol, use the distance command. An example and the command syntax are shown below:
router(config)#router rip
router(config-router)#distance 125
The complete syntax of the distance command is:
distance weight [address mask [ access-list-number | name]
The weight parameter is the AD, which can be a number from 10 to 255. Note that distances 0 through 9 are reserved for system use.
To change only the AD for selected networks, use an access list with the distance command as shown below:
router(config)# access-list 5 permit 10.0.0.0 255.0.0.0
router(config)# access-list 5 permit 11.0.0.0 255.0.0.0
router(config)# access-list 5 permit 12.0.0.0 255.0.0.0
router(config)# router rip
router(config-router)# distance 220 0.0.0.0 255.255.255.255 5
The 0.0.0.0 255.255.255.255 portion included with the distance command could hold an address/mask combination for a single address, but it is more common to use an access list.
Objective:
Layer 3 Technologies
Sub-Objective:
Configure and verify redistribution between any routing protocols or routing sources
References:
Cisco > Cisco IOS IP Routing: Protocol-Independent Command Reference > distance (ip) Cisco > Support > Technology Support > IP > IP Routing > Design > Design Technotes > What Is Administrative Distance? > Document ID: 26634
Question 7:
Refer to the exhibit. ISP 1 and ISP 2 directly connect to the Internet. A customer is tracking both ISP links to achieve redundancy and cannot see the Cisco IOS IP SLA tracking output on the router console.
Which command is missing from the IP SLA configuration?
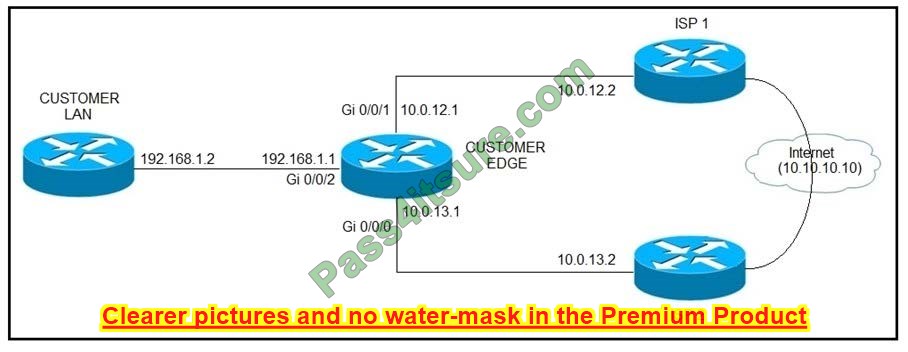
A. Start-time 00:00
B. Start-time 0
C. Start-time immediately
D. Start-time now
Correct Answer: D
Question 8:
DRAG DROP
Drag and drop the BGP states from the left to the matching definitions on the right.
Select and Place:
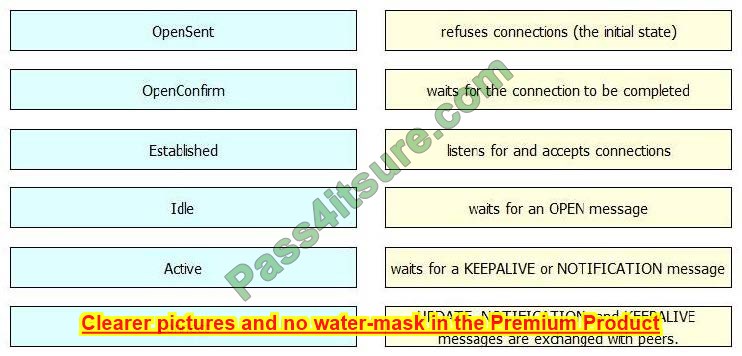
Correct Answer:


Question 9:
Refer to the exhibit.

Which statement about R1 is true?
A. OSPF redistributes RIP routes only if they have a tag of one.
B. RIP learned routes are distributed to OSPF with a tag value of one.
C. R1 adds one to the metric for RIP learned routes before redistributing to OSPF.
D. RIP routes are redistributed to OSPF without any changes.
Correct Answer: B
Question 10:
Which feature of the Cisco DNA Center allows you to run diagnostic CLI commands to the devices that are managed by DNA Center for troubleshooting purposes?
A. Command Runner
B. DNA Spaces
C. DNA Advantage
D. Intelligent Capture
Correct Answer: A
Question 11 (2023 labs):
Refer to the following set of commands:
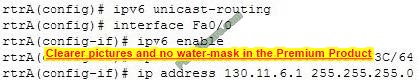
Which of the following statements is TRUE about the given set of commands?
A. IPv4 and IPv6 are running simultaneously on rtrA
B. The IPv4 address is translated to an IPv6 address
C. The IPv6 address is an IPv4-compatible address
D. A tunnel is created for the interoperability of the IPv4 and IPv6 addresses
Correct Answer: A
The correct answer is that IPv4 and IPv6 are running simultaneously on rtrA. The set of commands enables IPv6 on the rtrA router and assigns an IPv4 address and an IPv6 address to the Fa0/0 interface. This indicates that the router is a
dual-stack router on which both IPv4 and IPv6 are running simultaneously.
The IPv4 address is not translated to the IPv6 address by the given set of commands because NAT-PT is not enabled on the router. To enable NAT-PT on a router, you need to use the ipv6 nat command. In addition, the ipv6 nat prefix
command should be used to specify an IPv6 prefix.
The IPv6 address is not an IPv4-compatible address. IPv4-compatible IPv6 addresses are used in automatic IPv4-compatible IPv6 tunnels. These addresses refer to those IPv6 unicast addresses that have zeros in the first 96 bits and an
IPv4 address in the last 32 bits. For example, 0:0:0:0:0:0:192.156.10.67 is an IPv4- compatible IPv6 address where 192.156.10.67 is an IPv4 address. The IPv6 address (2001:0:1:1:D52::F3C/64), in this case, is not an IPv4-compatible IPv6
address.
A tunnel is not created for the interoperability of the IPv4 and IPv6 addresses because the given set of commands configures the router as a dual-stack router. There are no commands for configuring a tunnel on the router.
Objective:
Network Principles
Sub-Objective:
Recognize proposed changes to the network
References:
Cisco IOS IPv6 Configuration Guide, Release 12.4 > Implementing IPv6 Addressing and Basic Connectivity > Configuration Examples for Implementing IPv6 Addressing and Basic Connectivity > Example: Dual Protocol Stacks Configuration
Question 12:
Refer to the exhibit.

The security department recently installed a monitoring device between routers R3 and R5, which a loss of network connectivity for users connected to R5. Troubleshooting revealed that the monitoring device cannot forward multicast packets.
The team already updated R5 with the correct configuration. Which configuration must be implemented on R3 to resolve the problem by ensuring R3 is the DR for the R3-R5 segment?
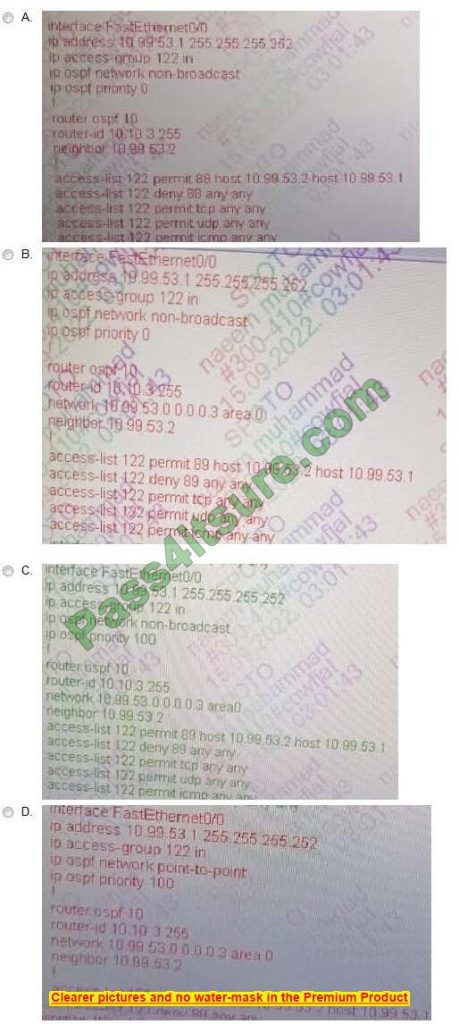
A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: C
Question 13:
Refer to the exhibit.

When the FastEthemet0/1 goes down, the route to 172.29.0.0/16 via 192.168.253.2 is not installed in the RIB, Which action resolves the issue?
A. Configure a feasible distance greater than the successor\’s feasible distance.
B. Configure reported distance greater than the successor\’s feasible distance.
C. Configure a feasible distance greater than the reported distance.
D. Configure the reported distance greater than the feasible distance.
Correct Answer: C
From the exhibit, we notice network 172.29.0.0/16 was learned via two routes:
+ From 192.168.254.2 with FD = 307200 and AD = 281600 + From 192.168.253.2 with FD = 410200 and AD = 352300
The first route is installed into the RIB as the successor route because of lower FD. When the first route fails, the router will not use the second route as it does not satisfy the feasibility condition. The feasibility condition states that the Advertised Distance (AD, also called the reported distance) of a route must be lower than the feasible distance of the current successor route.
Question 14 (2023 labs):
Your company has implemented IPv6 addresses and routing on every host, server, and router. Recently, your company acquired another company that has an IPv4 addressing scheme for its entire network.
The acquired company\’s network does not have any support for IPv6. You need to devise a method so that the IPv6 hosts in your company can seamlessly communicate with the IPv4 hosts of the acquired company\’s network.
You do not want to install any additional routers, and you want minimum configuration changes on the networks. Which of the following is the best method to allow communication between the IPv4 and IPv6 hosts?
A. Embedding IPv6 packets into IPv4 packets
B. Translating IPv4 addresses to and from IPv6 addresses
C. Configuring IPv6 on the hosts and routers in the IPv4 network
D. ConfiguringIPv4 on the hosts and routers in the IPv6 network
Correct Answer: B
Translating IPv4 addresses to and from IPv6 addresses is the best method to allow communication between the IPv4 and IPv6 hosts. This translation of IPv4 and IPv6 addresses is known as Network Address Translation-Protocol Translation
(NAT-PT). NAT-PT is a technique available for deploying IPv6 and IPv4 addresses in a unified network. With NAT-PT, the network requires fewer modifications and software for the IPv4 and IPv6 hosts. Additionally, it provides easy and quick
interoperability between the IPv4 and IPv6 hosts.
NAT-PT is configured on one of the routers on the border of the IPv4 and IPv6 networks. Whenever an IPv4 packet intended for a host in the IPv6 network is received by the NAT-PT router, the router applies NAT-PT on the packet and
translates all the headers in the IPv4 headers. In addition, it translates the IPv4 source and destination addresses to IPv6 source and destination addresses. The IPv6 packet is then set by the NAT-PT router to the intended IPv6 host. The
NAT-PT router performs the reverse translation when an IPv6 host sends a packet to an IPv4 host.
Embedding IPv6 packets into IPv4 packets is not the best method to allow communication between the IPv4 and IPv6 hosts. When IPv6 packets are embedded inside IPv4 packets, the process is referred to as tunneling. Tunneling is
appropriate when two IPv6 networks are separated by an IPv4 network. When an IPv6 host of one network sends an IPv6 packet destined for a host on the other IPv6 network, an IPv4 tunnel is created between the two IPv6 networks.
The IPv6 packet is then embedded into an IPv4 packet that traverses through the IPv4 tunnel to reach the intended IPv6 host, where the embedded packet is extracted by the recipient. In this scenario, a single IPv6 network is available; hence, a tunnel cannot be formed.
Configuring IPv6 on the hosts and routers in the IPv4 network, or configuring IPv4 on the hosts and routers in the IPv6 network, are not the best methods to allow communication between the IPv4 and IPv6 hosts. Each of these two methods is cumbersome and not the most efficient for providing interoperability between IPv4 and IPv6 in this case. Furthermore, the IPv4 hosts on the acquired company\’s network do not support IPv6 as stated.
Objective:
Network Principles
Sub-Objective:
Recognize proposed changes to the network
References:
Cisco NAT Configuration Guide, Release 15MandT > NAT-PT for IPv6
Question 15:
Refer to the exhibit.
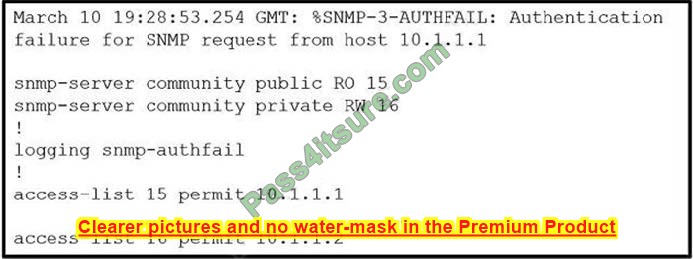
Which action resolves the issue?
A. Configure host IP address in access-list 16.
B. Configure SNMPv3 on the router.
C. Configure SNMP authentication on the router.
D. Configure a valid SNMP community string.
Correct Answer: D
…
New 300-410 dumps are the best exam material for your exam preparation, you only need 3-5 days of practice preparation to help you pass the CCNP Enterprise ENARSI certification exam!
Download New 300-410 dumps: https://www.pass4itsure.com/300-410.html, use PDF or VCE tools to help you learn easily! Guarantee that you will pass the CCNP Enterprise ENARSI certification exam 100% successfully.