[New Questions] Best Training for High Pass Rate Cisco 200-155 Dumps DCICT PDF Exam Video Test Questions Latest Version PDF&VCE (Question 1 – Question 28)
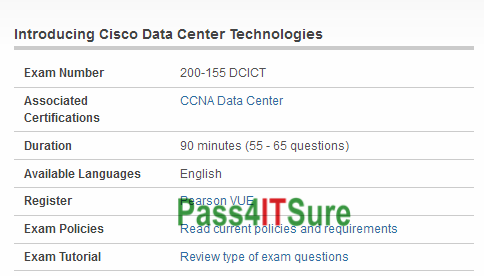
What am I going to be tested for Cisco 200-155 dumps exam? The Introducing Cisco Data Center Technologies (200-155 DCICT) exam is a 90 minutes (55 – 65 questions) assessment in pass4itsure that is associated with the CCNA Data Center certification. Best training for high pass rate Cisco 200-155 dumps DCICT pdf exam video test questions latest version pdf&vce. “Introducing Cisco Data Center Technologies” is the exam name of Pass4itsure Cisco 200-155 dumps test which designed to help candidates prepare for and pass the Cisco 200-155 exam. Our Cisco certification 200-155 DCICT training material dumps are very popular among customers and this is the result of Pass4itsure expert team industrious labor. The simulation test and the answer of their research have a high quality and have 95% similarity with the true https://www.pass4itsure.com/200-155.html dumps examination questions.
[New Pass4itsure 200-155 Dumps Questions From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWNHFtR0VqbXVEeUU
[New Pass4itsure 300-206 Dumps Questions From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWam9uZE5CQl9jczA
Kill your exam with Cisco 200-155 dumps real questions(1-28)
QUESTION 8
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of. He wants to use Kismet as a wireless sniffer to sniff the We-are-secure network. Which of the following IEEE-based traffic can be sniffed with Kismet?
A. 802.11g
B. 802.11n
C. 802.11b
D. 802.11a
200-155 exam Correct Answer: ABCD
Explanation
Explanation/Reference:
Explanation:
Kismet can sniff IEEE 802.11a, 802.11b, 802.11g, and 802.11n-based wireless network traffic.
QUESTION 9
Which of the following statements about the traceroute utility are true?
A. It uses ICMP echo packets to display the Fully Qualified Domain Name (FQDN) and the IP address of each gateway along the route to the remote host.
B. It records the time taken for a round trip for each packet at each router.
C. It is an online tool that performs polymorphic shell code attacks.
D. It generates a buffer overflow exploit by transforming an attack shell code so that the new attack shell code cannot be recognized by any Intrusion Detection Systems.
Correct Answer: AB
Explanation
Explanation/Reference:
Explanation:
Traceroute is a route-tracing utility that displays the path an IP packet takes to reach its destination. It uses ICMP echo packets to display the Fully Qualified Domain Name (FQDN) and the IP address of each gateway along the route to the remote host. This tool also records the time taken for a round trip for each packet at each router that can be used to find any faulty router along the path. Answer: C, D are incorrect. Traceroute does not perform polymorphic shell code attacks. Attacking tools such as ADMutate areused to perform polymorphic shell code attacks.
QUESTION 10
George works as an office assistant in Soft Well Inc. The company uses the Windows Vista operating system. He wants to disable a program running on a computer. Which of the following Windows Defender tools will he use to accomplish the task?
A. Allowed items
B. Quarantined items
C. Options
D. Software Explorer
200-155 dumps Correct Answer: D
Explanation
Explanation/Reference:
Explanation:
Software Explorer is used to remove, enable, or disable a program running on a computer. Answer: A is incorrect. Allowed items contains a list of all the programs that a user has chosen not to monitor with Windows Defender. Answer: C is incorrect. Options is used to choose how Windows Defender should monitor all the programs running on a computer. Answer: B is incorrect. Quarantined items is used to remove or restore a program blocked by Windows Defender.
QUESTION 11
You work as a Network Administrator for XYZ CORP. The company has a Windows Active Directory-based single domain single forest network. The functional level of the forest is Windows Server 2003. The company’s management has decided to provide laptops to its sales team members. These laptops are equipped with smart card readers. The laptops will be configured as wireless network clients. You are required to accomplish the following tasks: The wireless network communication should be secured. The laptop users should be able to use smart cards for getting authenticated. In order to accomplish the tasks, you take the following steps: Configure 802.1x and WEP for the wireless connections. Configure the PEAP-MS-CHAP v2 protocol for authentication. What will happen after you have taken these steps?
A. Both tasks will be accomplished.
B. The laptop users will be able to use smart cards for getting authenticated.
C. The wireless network communication will be secured.
D. None of the tasks will be accomplished.
Correct Answer: C
Explanation
Explanation/Reference:
Explanation:
As 802.1x and WEP are configured, this step will enable the secure wireless network communication. For authentication, you have configured the PEAP-MS-CHAP v2 protocol. This protocol can be used for authentication on wireless networks, but it cannot use a public key infrastructure (PKI). No certificate can be issued without a PKI. Smart cards cannot be used for authentication without certificates. Hence, the laptop users will not be able to use smart cards for getting authenticated.
QUESTION 12
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to print the super block and block the group information for the filesystem present on a system. Which of the following Unix commands can you use to accomplish the task?
A. e2fsck
B. dump
C. dumpe2fs
D. e2label
200-155 pdf Correct Answer: C
Explanation
Explanation/Reference:
Explanation:
In Unix, the dumpe2fs command dumps the filesystem superblock and blocks the group information. Answer: B is incorrect. In Unix, the dump command is used to back up an ext2 filesystem. Answer: A is incorrect. The e2fsck command is used to check the second extended file system (E2FS) of a Linux computer. Syntax: e2fsck [options] <device> Where, <device> is the file name of a mounted storage device (for example, /dev/hda1). Several options are used with the e2fsck command. Following is a list of some important options: C:\Documents and Settings\user-nwz\Desktop\1.JPG Answer: D is incorrect. In Unix, the e2label command is used to change the label of an ext2 filesystem.
QUESTION 13
Which of the following is a wireless auditing tool that is used to pinpoint the actual physical location of wireless devices in the network?
A. KisMAC
B. Ekahau
C. Kismet
D. AirSnort
Correct Answer: B
Explanation
Explanation/Reference:
Explanation:
Ekahau is an easy-to-use powerful and comprehensive tool for network site surveys and optimization. It is an auditing tool that can be used to pinpoint the actual physical location of wireless devices in the network. This tool can be used to make a map of the office and then perform the survey of the office. In the process, if one finds an unknown node, ekahau can be used to locate that node. Answer: D is incorrect. AirSnort is a Linux-based WLAN WEP cracking tool that recovers encryption keys. AirSnort operates by passively monitoring transmissions. It uses Ciphertext Only Attack and captures approximately 5 to 10 million packets to decrypt the WEP keys. Answer: C is incorrect. Kismet is a Linux-based 802.11 wireless network
sniffer and intrusion detection system. It can work with any wireless card that supports raw monitoring (rfmon) mode. Kismet can sniff 802.11b, 802.11a, 802.11g, and 802.11n traffic. Kismet can be used for the following tasks: To identify networks by passively collecting packets To detect standard named networks To detect masked networks To collect the presence of non-beaconing networks via data traffic Answer: A is incorrect. KisMAC is a wireless network discovery tool for Mac OS X. It has a wide range of features, similar to those of Kismet, its Linux/BSD namesake and far exceeding those of NetStumbler, its closest equivalent on Windows. The program is geared toward network security professionals, and is not as
novice-friendly as similar applications. KisMAC will scan for networks passively on supported cards – including Apple’s AirPort, and AirPort Extreme, and many third-party cards, and actively on any card supported by Mac OS X itself. Cracking of WEP and WPA keys, both by brute force, and exploiting flaws such as weak scheduling and badly generated keys is supported when a card capable of monitor mode is used, and packet reinjection can be done with a supported card. GPS mapping can be performed when an NMEA compatible GPS receiver is attached. Data can also be saved in pcap format and loaded into programs such as Wireshark.
QUESTION 14 Which of the following authentication modes does VRRP use?
A. No authentication
B. Simple text password
C. MD5
D. CHAP
200-155 vce Answer: ABC
QUESTION 15 Which of the following configurations can be performed to implement fast failure detection on a network?
A. Reduce the holdtime of Join/Prune messages.
B. Reduce the interval for an interface to send Hello messages.
C. Set up a PIM BFD session between network segment neighbors.
D. Reduce the interval for sending Join/Prune messages.
Answer: BC
QUESTION 16 Which of the following statements are correct regarding default gateway in the network running VRRP?
A. Configure only one gateway for the PC which is the IP address of Master.
B. Configure only one gateway for the PC which is the IP address of virtual router.
C. Configure two gateways for the Pc which are the IP addresses of Master slave.
D. Configure three gateways for the PC which are the IP addresses of Master, and virtual router.
200-155 exam Answer: B
QUESTION 17.Which of the following technologies can reduce the scale of broadcast domain?
A. VLAN
B. Trunk
C. RARP
D. STP
Answer: A
QUESTION 18.Which are the functions of the route target on an MPLS VPN network?
A. Enable the peer PE to determine whichVPNv4 routes can be imported to the specified VRF.
B. Enable the peer PE to determine whichVPNv4 routes cannot be imported to the specified VRF.
C. Enable the peer CE to determine whichVPNv4 routes can be imported to the specified VRF.
D. Enable the peer CE to determine whichVPNv4 routes cannot be imported to the specified VRF.
200-155 dumps Answer: AB
QUESTION 19.Which statement about the trunk interface is true?
A. A trunk interface is always connected to hosts.
B. Multiple VLAN IDs can be set on a trunk interface. The VLAN IDs can be the same as or different from the PVID.
C. The trunk interface cannot have a PVID.
D. If the trunk interface receives a packet with a VLAN not in the allowed VLAN list, the trunk interface broadcast the packet in the VLAN.
Answer: B
QUESTION 20.Which of the following are factors that affect QoS?
A. Bandwidth
B. Delay
C. Jitter
D. Loss of packet
200-155 pdf Answer: ABCD
QUESTION 21.IP network can provide various packet forwarding service, the service demands that users care during packet forwarding include .
A. Throughput
B. Delay
C. Jitter
D. Loss of packet
Answer: ABCD
QUESTION 22.IP QoS models include:
A. Best-Effort
B. Integrated Service
C. Differentiated Service
D. FIFO Service Answer:
200-155 vce Answer:ABC
QUESTION 23.QoS can provide different quality of service according to different demands, which of the following are functions of QoS?
A. Providing private bandwidth for users
B. Reducing loss of packet
C. Congestion management and avoidance
D. Specifying priority of packets
Answer: ABCD
QUESTION 24.What is the legal virtual MAC address in VRRP?
A. 01-01-5E-OO-Ol-OI
B. 01-00-5E-OO-OI-OO
C. 00-00-5E-OO-Ol-01
D. 01-01-5E-OO-OO-OI
200-155 exam Answer: C
QUESTION 25.Which of the following statements are correct regarding Master in VRRP?
A. The router with highest priority will become Master.
B. The router with smallest priority will become Slave.
C. The router with highest priority may not always be Master.
D. The router with smallest priority may not always be Slave.
Answer: CD
QUESTION 26.Which of the following statements are correct regarding priority in VRRP?
A. The IP address owner always uses 255 as its priority regardless its config priority.
B. The IP address owner always uses o as its priority regardless its config priority.
C. We can configure the priority as o to make the router never attend the Master election.
D. If a VRRP router changes from Master to Slave, it will send out a VRRP message with priority o in the network.
200-155 dumps Answer: A
QUESTION 27.Which of the following statements are correct regarding VRRP?
A. Only Master can process the data packets sending to virtual router.
B. Only Slave can process the data packets sending to virtual router.
C. Both Master and Slave can process the data packets sending to the same virtual router to realize load balance.
D. By default, only Master can process the data packets sending to virtual router; but we can do some configuration to make the Slave process the data packets sending to virtual router.
Answer: A
QUESTION 28.Which of the following statements are correct regarding the function of VRRP?
A. VRRP can improve the reliability of default gateway.
B. VRRP increase the convergence speed of routing protocol.
C. VRRP is mainly used for traffic balance.
D. VRRP can provide one default gateway for different network segments, it simplifies the gateway configuration for PC.
200-155 pdf Answer: A
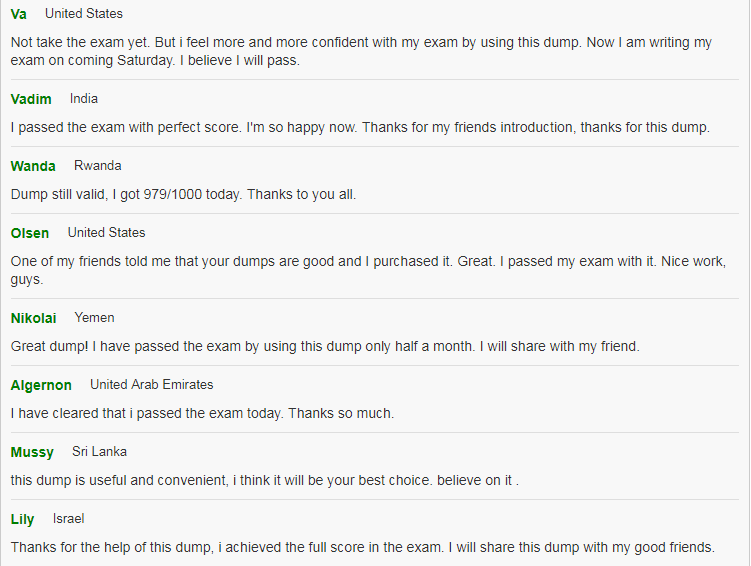
See What Our Customers Are Saying:
We at Pass4itsure are committed to our customer’s success. There are 50,000+ customers who used this preparation material for the preparation of various certification exams and this number of customers is enough for new candidates to trust in these products.Our Cisco 200-155 dumps are created with utmost care and professionalism. We utilize the experience and knowledge of a team of industry professionals from leading organizations all over the world.
Pass4itsure have a strong It expert team to constantly provide you with an effective training resource. They continue to use their rich experience and knowledge to study the real 200-155 dumps exam questions of the past few years. “Introducing Cisco Data Center Technologies”, also known as 200-155 exam, is a Cisco certification which covers all the knowledge points of the real Cisco exam. Pass4itsure Cisco 200-155 dumps exam questions answers are updated (85 Q&As) are verified by experts. The associated certifications of 200-155 dumps is CCNA Data Center. Finally Pass4itsure targeted Cisco certification 200-155 DCICT training material dumps have advent, which will give a great help to a lot of people participating in the IT certification exams. Pass4itsure expert team use their experience and knowledge to study the examinations of past years and finally have developed the best Cisco certification https://www.pass4itsure.com/200-155.html dumps DCICT training material dumps.
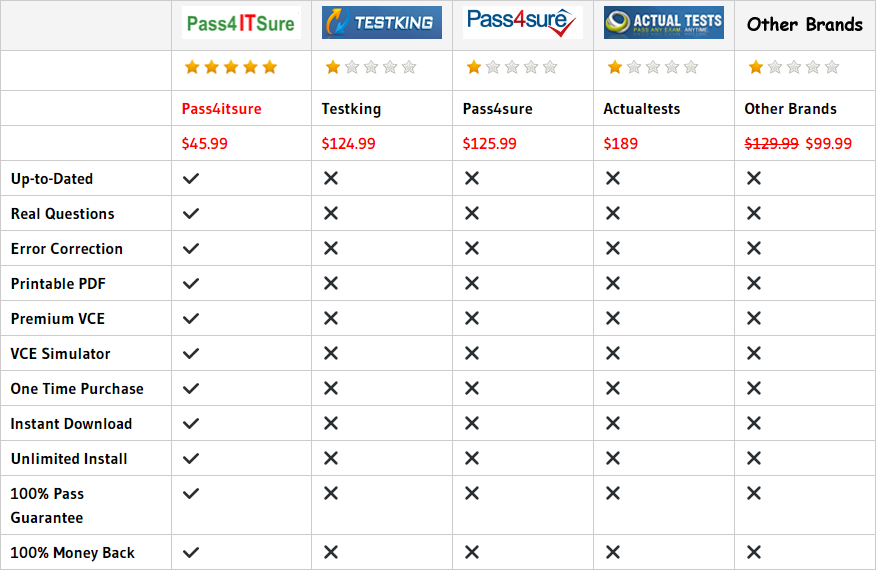
Compared with other brands, Pass4itsure has up to dated exam information, affordable price, instant exam PDF files downloaded, error correction, unlimited install,etc. Such as Pass4itsure High Pass Rate Cisco 200-155 Dumps Exam Test Questions, Real Cisco 200-155 Dumps Latest Version PDF&VCE, We Help You Pass Introducing Cisco Data Center Technologies. Simple and Easy! To take advantage of the guarantee, simply contact Customer Support, requesting the exam you would like to claim. Pass4itsure guarantee insures your success otherwise get your MONEYBACK!